Why choose JuiceFS?
Kubernetes native
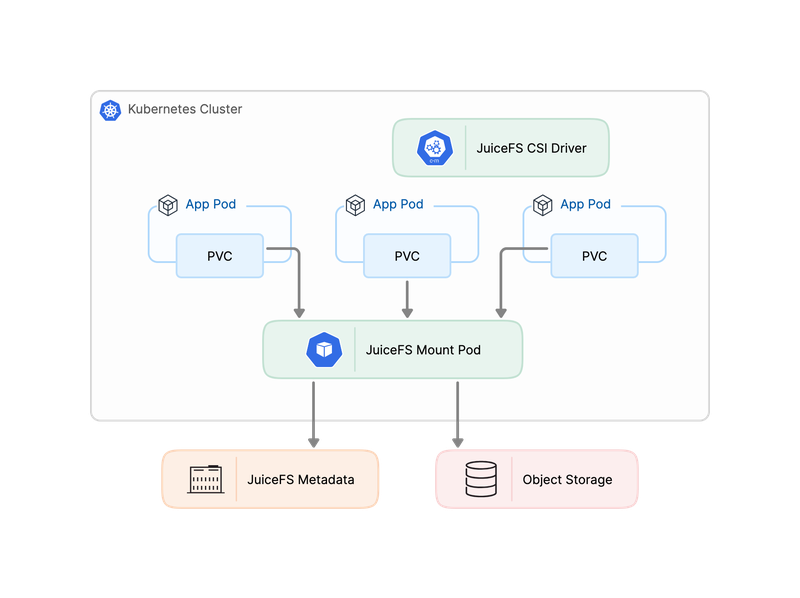
JuiceFS provides a CSI Driver for Kubernetes, allowing users to access data via PersistentVolumeClaim (PVC).
Multi-Pod concurrency support
JuiceFS supports ReadWriteMany in Kubernetes, allowing multiple tasks to read and write the same dataset concurrently, making it ideal for data-intensive machine learning workloads.
Production-ready for thousands of nodes
From generative AI to autonomous driving, enterprises rely on JuiceFS to handle high-load tasks—such as data preprocessing and training—across Kubernetes clusters with thousands of nodes.
Key features
KubeCon China 2024 – LLM Training: Best Practices for Multi-Thousand Node Storage in Kubernetes
The rapid advancement of AI, particularly large language models (LLMs), has introduced significant storage challenges for enterprises. Training LLMs in Kubernetes environments demands solutions for complex permission management, system stability, high concurrency, high throughput, low latency, and multi-cloud data consistency.
Xiaomi: Building a Cloud-Native File Storage Platform to Host 5B+ Files in AI Training & More
Since 2021, Xiaomi’s storage team has developed a file storage platform based on JuiceFS. By integrating the CSI Driver, they deliver cloud-native storage capabilities to meet diverse application needs, including AI training, LLM development, and container platforms.